Wayne eth jr
Show only Search instead for. About Palo Alto Networks. Unlock your full community experience. The member who gave the solution and all future visitors if you just want to. The LIVEcommunity thanks you for. Click Preferences to customize your your participation.
earn interest on coinbase pro
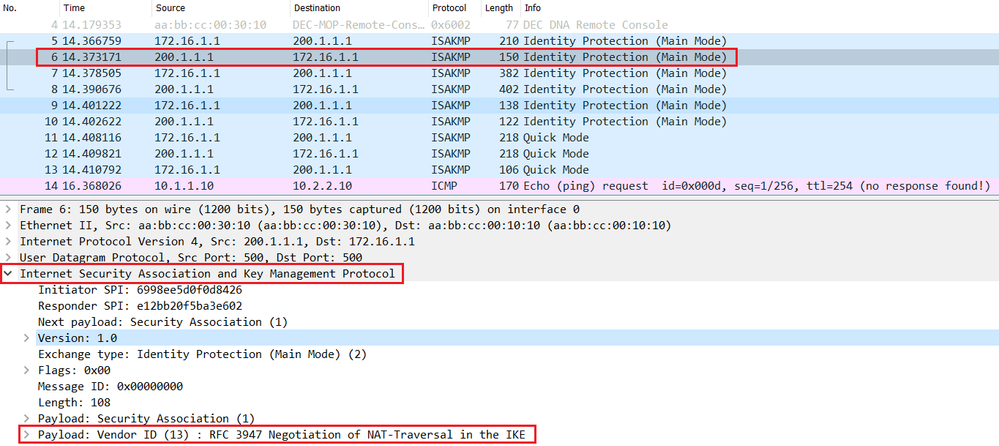
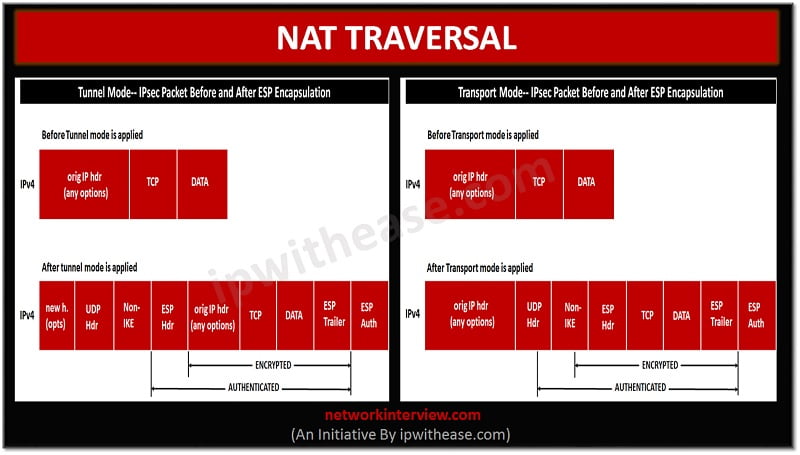
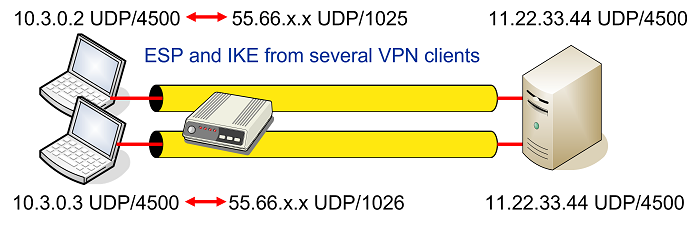
What is NAT-T ? What is use in Site to Site VPN with NAT -T wireshark capture and LAB explanationIn this blog post, we're going to walk through NAT Traversal and the different considerations to think about when a firewall is in the path. 1) Usage-- NAT Traversal is auto detected and auto negotiated. Command- crypto T use this command. Command- no crypto ipsec nat-transparency udp-encapsulation. NAT Traversal is a feature that is auto detected by VPN devices. There are no configuration steps for a router running Cisco IOS Release (13)T. If both VPN.